In late February, an international law enforcement group known as the NCA (National Crime Agency) banded together to execute 'Operation Cronos' to take down the Ransomware as a Service group known as LockBit. The LockBit group emerged in 2019 and has largely been one of the dominating Ransomware as a Service groups. The Department of Justice explains that LockBit operates with a hierarchy where administrators, also referred to as developers, create the ransomware, enlist members—termed affiliates—to spread it, and oversee a digital "control panel" to equip these affiliates with the necessary tools for deployment. These affiliates, in their turn, scout for and illegally access vulnerable computer systems, either through direct hacking or by buying stolen credentials. Through the control panel, they launch LockBit, encrypting and extracting data from the targeted systems, and then demand a ransom to decrypt the data or refrain from publishing it on a publicly accessible data leak site managed by the LockBit developers. Affiliates earn a commission for each ransom paid, showing the 'as a service' business model's nefarious adaptation to cybercrime.
In 2023, it was estimated to account for 44% of ransomware incidents globally. It’s obvious that this is a growing problem.
During Operation Cronos, which took over a month to execute, law enforcement successfully infiltrated and took control of LockBit's servers and administrative portals. They uncovered data belonging to victims, including those who had paid ransoms but had not received their data. TechTarget quotes the NCA: "Some of the data on LockBit's systems belonged to victims who had paid a ransom to the threat actors, evidencing that even when a ransom is paid, it does not guarantee that data will be deleted, despite what the criminals have promised."
 LockBit Access Screen Photo Credit: 360 SOC
LockBit Access Screen Photo Credit: 360 SOC
The unfortunate reality is that businesses fall victim to this every day. At Prime Secured, we often onboard organizations as clients because they reach out to us after losing their data, with some having paid the ransom and others not. Our goal is to assist them in damage control and data recovery.
As of March 1st, it is reported that LockBit has rebuilt their infrastructure and is exploiting new victims' data. Thankfully, they lost everything that they had previously stolen, but that’s not stopping them from rebuilding.
Groups like LockBit are running rampant; it's not a model or tactic that is going away anytime soon. The NCA and task forces alike are still going to be in a continuous fight; once they put out one fire, another starts to burn. We share all of this to educate you and your organization on the different measures that can be implemented today to prevent the fire from happening in your building. We've compiled a list of preventive measures ranging from simple, immediate actions to more sophisticated solutions that might require internal expertise or the involvement of a third-party provider like Prime Secured.
So up first, our easy to implement with little to no experience suggestions:
Educate Your Workforce: One of the simplest ways that will have a huge impact is to regularly train employees on cybersecurity best practices, including how to recognize phishing emails and the importance of not clicking on suspicious links or attachments. Here is a list of resources to get you going in providing a training program to your employees.
- Protect from Within: How to Prioritize Employee Cybersecurity Training
- 7 Tips to Boost Your Cybersecurity Training Program for Remote Workers
- Stop Ransomware: Your Checklist to Mitigate Malware Attacks
- How to Spot an Email Scam
- 5 Tips to Improve Cybersecurity Training Engagement
- How to Prevent Phishing Emails
- How to Recognize a Business Email Compromise (BEC) Attack
- 10 Best Practices for Ongoing & Effective Cybersecurity Training
Implement Strong Password Policies: We’ve preached this time and time again, but we strongly suggest the use of complex passwords and mandate periodic changes. Consider implementing multi-factor authentication (MFA) to add an extra layer of security. Here are our resources dedicated to password best practices:
Regular Updates: Keep your operating system, software, and any installed apps up to date. This can often be automated or accomplished with simple prompts from the software itself. Regularly restart your computer and browser to ensure updates take effect. Here are a few simple steps you can follow to maintain a healthy & secure computer: How to Maintain a Healthy Computer.
Antivirus Software: Install reputable antivirus software and ensure it is set to update automatically. Running regular scans can often be done with minimal setup.
Data Backup: Regularly back up important data. This can be as simple as using a cloud service that automatically syncs your files or using an external hard drive and manually copying over important files.
Ready for More Ransomware Prevention Strategies?
Depending on the size and needs of your organization, these steps may be enough to keep your business protected. However, if you have a more complex network with more employees, there are additional measures that can be put in place, but these typically require the help of a dedicated internal resource or an outside provider.
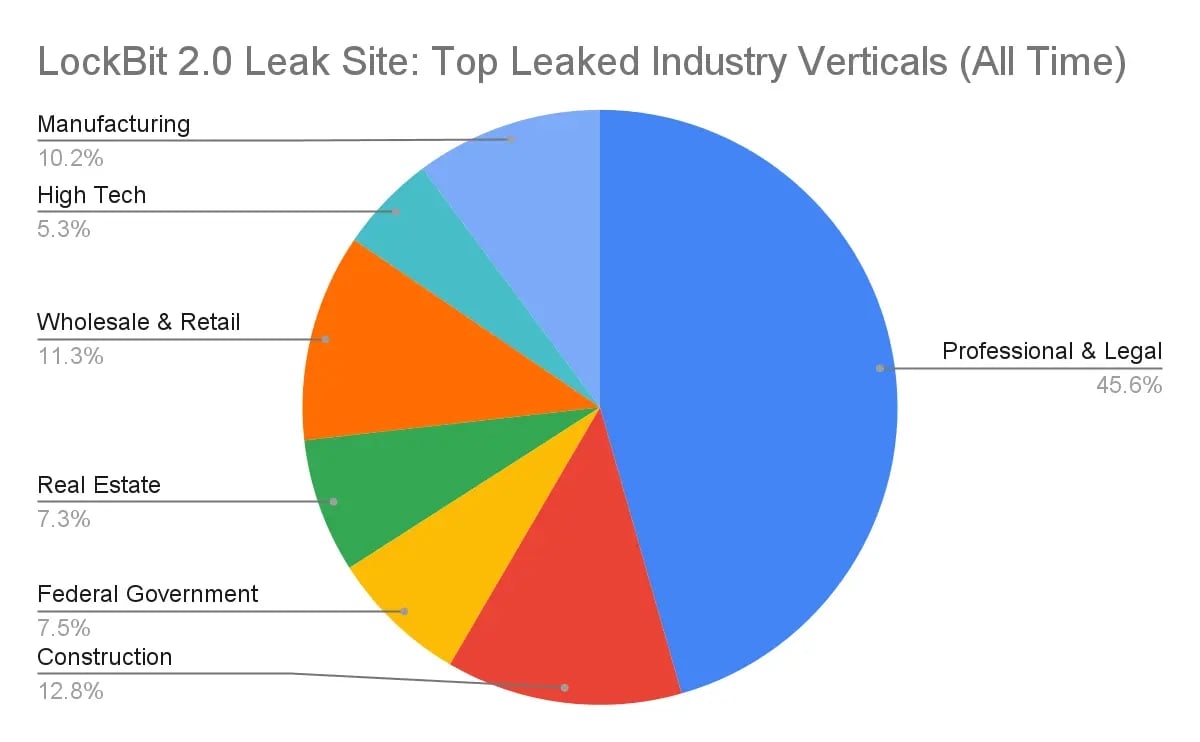 LockBit 2.0 impacted industry vertical chart. Photo Credit: Unit 42 by Palo Alto Networks
LockBit 2.0 impacted industry vertical chart. Photo Credit: Unit 42 by Palo Alto Networks
Here is our list of advanced suggestions that can be implemented by an expert.
Network Segmentation: Network segmentation is essential in the event of a ransomware attack. Although we hope it never occurs, if it does, having implemented network segmentation isolates the risk, preventing the attack from spreading further. What network segmentation does is divide your network into smaller, manageable segments to limit the spread of ransomware. However, it requires a good understanding of network architecture and access controls.
Custom Security Policies and Group Policies: These are crucial measures designed to define and enforce security within an organization's networks and systems. These policies manage user access and system configurations, significantly reducing the risk of ransomware attacks by limiting potential entry points and vulnerabilities. By controlling user behaviors and ensuring devices comply with security standards, they minimize the attack surface that ransomware can exploit. Implementing these policies requires a deep understanding of network security.
Advanced Endpoint Detection and Response (EDR): Implementing and managing EDR solutions requires technical know-how to monitor, analyze, and respond to threats in real-time. This is a vital prevention measure as it can detect and prevent malware infections.
Implementing a Secure Email Gateway: Setting up advanced email filtering rules and scanning for threats to prevent phishing and malware can help prevent malicious emails from ever reaching an inbox, thus eliminating the risk of human error from mistakenly clicking on a link they shouldn't. Learn more about how tools like this work: How to Prevent Phishing Emails.
Encryption Management: Implementing and managing encryption across various platforms and devices to protect sensitive data in transit makes your data more impenetrable and harder to steal.
Regularly Conducting Vulnerability Assessments & Penetration Testing (VAPT): Just as ransomware groups like LockBit learn from their errors to continually rebuild and become more challenging to take down, organizations must do the same to keep up. Regularly conducting Vulnerability Assessment and Penetration Testing (VAPT) is an effective way to identify and address weaknesses that may not even be known. A vulnerability assessment systematically identifies, quantifies, and prioritizes vulnerabilities in your systems, providing an overview of potential security flaws. In contrast, a penetration test simulates a cyberattack against your system to exploit these vulnerabilities, testing the effectiveness of your security measures. Together, these processes help organizations stay one step ahead of threats by uncovering and mitigating risks before they can be exploited.
Ready to Stop Ransomware as a Service Groups from Exploiting You?
We've provided you with implementations that can be executed today, along with a list of more serious measures that we highly recommend implementing with the help of an expert. If you are looking for a trusted partner to implement these advanced measures, reach out to Prime. We are happy to provide a complimentary network assessment that will offer a starting point for understanding your cybersecurity posture and what the next steps for strengthening it are.
As discussed, Ransomware as a Service is not going anywhere anytime soon. While LockBit may meet its demise, other groups will continue the work. It's important to have a technology partner you trust, one that takes groups like this seriously and stays updated on what's happening in our current world.
If Prime Secured sounds like a good fit for you, call us at 402-289-4126 or reach out to us on our website.
Our Blog
Subscribe to the Prime Secured blog to receive the latest updates.